How IT Managers Can Balance Productivity and Security with New Software Adoption in 5 Steps
Imagine a world where your company’s software implementations are seamless, productivity soars, and security breaches are a thing of the past. Balancing software adoption, productivity, and security is key to achieving this vision.
As a life coach, I’ve helped many professionals navigate these challenges. In my experience helping clients stand out in competitive industries, I often encounter issues related to IT risk management and remote work software security.
In this article, you’ll discover proven strategies to balance productivity and security with new software adoption. We’ll cover actionable steps and insights to ensure a smooth transition, including employee productivity tools and data protection in new software.
Let’s dive in and explore software implementation strategies that prioritize cybersecurity for business applications.
Understanding the Challenges of Balancing Productivity and Security
Navigating new software adoption often feels like walking a tightrope. Many companies struggle with outdated systems that hinder productivity and pose security risks, making balancing software adoption productivity security a complex task.
These challenges can lead to significant inefficiencies and vulnerabilities in IT risk management.
I often see clients frustrated by resource limitations and the slow pace of technology adoption, especially when implementing remote work software security measures. The perception of IT within the organization can exacerbate the problem, creating resistance to change.
This resistance can lead to data breaches and employee dissatisfaction, highlighting the importance of effective software implementation strategies.
In my experience, addressing these issues requires a strategic approach. By understanding the root causes and potential impacts, you can better prepare for a successful software transition while balancing innovation and data privacy.
Strategic Steps for Balancing Productivity and Security in Software Adoption
Overcoming this challenge requires a few key steps. Here are the main areas to focus on to make progress in balancing software adoption productivity and security.
- Implement Phased Rollout with Pilot Groups: Start with a small, diverse group of users to test new software before a full rollout, aligning with IT risk management practices.
- Provide Comprehensive Training and Support: Develop various training materials and maintain ongoing support to help users adapt to employee productivity tools.
- Use Automated Security Testing in CI/CD Pipeline: Integrate automated security testing tools to detect vulnerabilities early, enhancing cybersecurity for business applications.
- Establish Clear Adoption Metrics and Feedback: Define KPIs for software adoption and gather user feedback to make adjustments, supporting effective software implementation strategies.
- Appoint Champions to Drive User Acceptance: Identify and train internal advocates to promote and support the new software, facilitating user training for new technology.
Let’s dive in!
1: Implement phased rollout with pilot groups
Introducing a phased rollout with pilot groups is crucial for balancing software adoption productivity security during new software implementation strategies.
Actionable Steps:
- Select a diverse pilot group: Choose a small, varied group of users to test the new software. Track their performance and gather feedback on employee productivity tools.
- Expand rollout gradually: Use the feedback and performance data to inform a broader rollout. Set specific milestones for each phase, considering IT risk management.
- Monitor and adjust: Continuously monitor the pilot group, making adjustments based on their feedback and ensuring data protection in new software.
Explanation: These steps matter because they help identify potential issues early, ensuring a smoother transition. Real-world data from pilot groups can shape the broader implementation strategy, reducing risks and improving cybersecurity for business applications.
According to a LinkedIn Pulse article, focusing on user-friendly technology and training is essential for successful adoption of remote work software security.
Key benefits of a phased rollout include:
- Minimized disruption to overall productivity
- Early identification of potential security risks
- Opportunity for fine-tuning before full deployment, considering IT policy for software adoption
By starting small and scaling up, you can maintain productivity and enhance security during the transition, effectively balancing software adoption productivity security.
Next, let’s explore the importance of comprehensive training and support in this process, including user training for new technology.

2: Provide comprehensive training and support
Providing comprehensive training and support is essential for balancing software adoption productivity security in any organization.
Actionable Steps:
- Develop diverse training materials: Create videos, manuals, and interactive sessions for employee productivity tools. Track attendance and completion rates for each type.
- Offer ongoing support: Set up helpdesks, online forums, and regular Q&A sessions for remote work software security. Monitor the number and types of support requests.
- Gather feedback: Collect user feedback through surveys and focus groups on software implementation strategies. Analyze the data to improve training programs.
Explanation: These steps matter because they help users quickly adapt to new software, minimizing disruptions while ensuring data protection in new software.
According to a source, consistent communication and training are crucial for successful technology adoption and IT risk management.
By offering varied training options and continuous support, you can ensure all users feel confident and capable with cybersecurity for business applications.
Next, let’s explore the importance of automated security testing in this process of balancing software adoption productivity security.

3: Use automated security testing in CI/CD pipeline
Incorporating automated security testing in your CI/CD pipeline is crucial for early detection of vulnerabilities and maintaining robust security, which is essential when balancing software adoption productivity security.
Actionable Steps:
- Integrate security testing tools: Choose compatible automated security testing tools and integrate them into your existing CI/CD pipeline. Monitor the number of vulnerabilities detected and resolved, focusing on IT risk management and cybersecurity for business applications.
- Conduct regular security audits: Schedule consistent security audits and threat modeling sessions to identify and mitigate risks. Document and review the results to ensure continuous improvement, especially for remote work software security and cloud-based software security measures.
Explanation: These steps matter because they help identify security issues early, reducing the risk of breaches. According to a NICE Framework, integrating cybersecurity objectives into project plans is essential for secure software development and balancing software adoption productivity security.
Regular security audits ensure that your systems remain secure and compliant with industry standards, supporting data protection in new software.
Key advantages of automated security testing:
- Continuous monitoring for vulnerabilities
- Faster detection and resolution of security issues
- Improved overall system reliability
By proactively addressing security in the development process, you can enhance both productivity and security, effectively balancing software adoption productivity security.
Next, let’s explore the importance of establishing clear adoption metrics and feedback.
4: Establish clear adoption metrics and feedback
Establishing clear adoption metrics and feedback is vital to ensure successful software implementation, particularly when balancing software adoption productivity security.
Actionable Steps:
- Define key performance indicators (KPIs): Identify specific KPIs for software adoption and usage, including IT risk management metrics. Set benchmarks and track progress against these indicators for employee productivity tools.
- Implement feedback loops: Regularly collect user feedback through surveys, focus groups, and interviews. Use this data to make iterative improvements and enhance data protection in new software.
- Analyze adoption data: Monitor and review usage statistics and feedback. Adjust software implementation strategies based on insights gained to enhance adoption rates and cybersecurity for business applications.
Explanation: These steps matter because they help measure success and identify areas for improvement in balancing innovation and data privacy.
According to a source, consistent feedback and metrics are crucial for effective technology adoption. By setting clear KPIs and leveraging user feedback, you can ensure a more efficient and secure transition, especially for remote work software security.
This approach ensures continuous improvement and adaptation, driving successful software adoption while maintaining IT policy for software adoption and implementing cloud-based software security measures.

5: Appoint champions to drive user acceptance
Appointing champions to drive user acceptance is crucial for the successful adoption of new software, particularly when balancing software adoption productivity security.
Actionable Steps:
- Identify and train influential champions: Select respected individuals within your organization and provide them with comprehensive training on the new software, including IT risk management and cybersecurity for business applications. Track their engagement and influence in promoting the software.
- Encourage champions to host workshops: Have these champions conduct workshops, demonstrations, and peer-to-peer training sessions on employee productivity tools and data protection in new software. Monitor attendance and gather feedback from these sessions to improve future training.
Explanation: These steps matter because champions can significantly influence their peers, making the transition smoother and aiding in software implementation strategies.
According to a source, having internal advocates helps drive user acceptance and improves adoption rates. By leveraging respected individuals, you can foster a culture of enthusiasm and support for the new software while addressing remote work software security concerns.
Characteristics of effective software champions:
- Strong communication and leadership skills
- Enthusiasm for new technologies and user training for new technology
- Ability to motivate and inspire colleagues while balancing innovation and data privacy
By appointing champions, you create a network of advocates who can guide and support others through the adoption process, ensuring IT policy for software adoption is followed and cloud-based software security measures are implemented.

Partner with Alleo for Seamless Software Adoption
We’ve explored the challenges of balancing software adoption productivity security in today’s rapidly evolving business landscape. Did you know you can work directly with Alleo to make this process easier and faster, while addressing IT risk management concerns?
Set up an account with Alleo and create a personalized plan for implementing software implementation strategies. Our AI life coach will guide you through each step, including user training for new technology and ensuring cloud-based software security measures.
Alleo provides tailored coaching, follow-ups, and accountability via text and push notifications to support your remote work software security and employee productivity tools adoption.
Ready to get started for free and improve your approach to balancing innovation and data privacy? Let me show you how!
Step 1: Log In or Create Your Account
To begin your journey towards seamless software adoption, log in to your existing Alleo account or create a new one to access our AI coach and personalized guidance.

Step 2: Choose “Building better habits and routines”
Click on “Building better habits and routines” to focus on creating consistent practices that will support your software adoption process, enhancing productivity and security in your organization.

Step 3: Select “Career” as Your Focus Area
Choose “Career” as your focus area to address software adoption challenges, enhance productivity, and strengthen security in your professional life. This selection aligns with the article’s emphasis on balancing these aspects in the workplace.

Step 4: Starting a coaching session
Begin your journey with Alleo by scheduling an intake session, where our AI coach will assess your software adoption challenges and create a personalized plan to guide you through the process, ensuring a smooth balance between productivity and security.

Step 5: Viewing and managing goals after the session
After your coaching session on software adoption strategies, check the Alleo app’s home page to review and manage the goals you discussed, helping you stay on track with implementing your new software rollout plan.
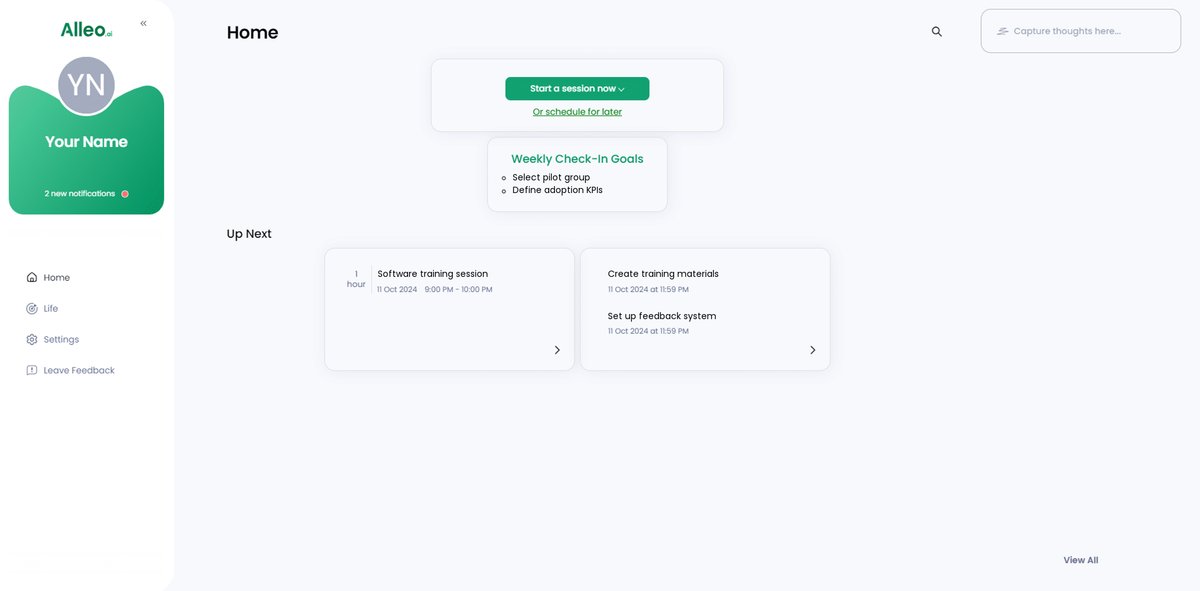
Step 6: Adding events to your calendar or app
Use Alleo’s calendar and task features to schedule and track your progress in implementing the new software, helping you maintain productivity while ensuring security measures are met throughout the adoption process.
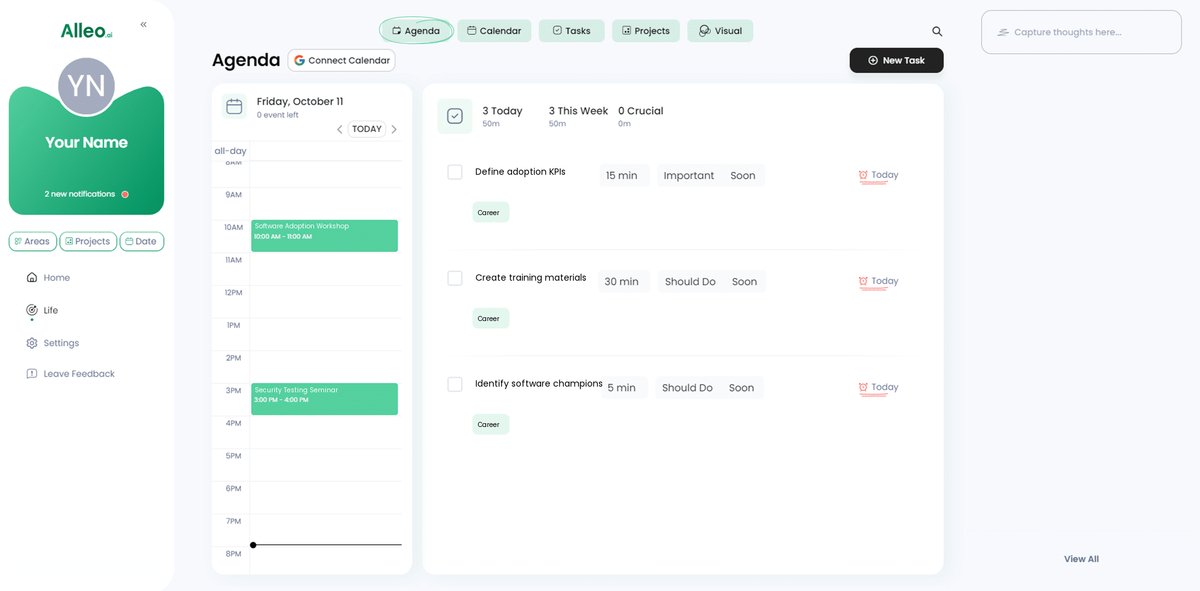
Achieving Seamless Software Adoption
We’ve covered a lot today. Balancing software adoption productivity security is challenging, but it’s achievable with effective IT risk management strategies.
By implementing phased rollouts, providing comprehensive user training for new technology, using automated security testing, establishing clear metrics, and appointing champions, you can ensure a smooth transition while maintaining data protection in new software.
Remember, you are not alone in this journey. Many face these challenges with remote work software security, but with the right software implementation strategies, you can overcome them.
Alleo is here to help. Our AI life coach can guide you through each step, ensuring your team stays productive and secure while balancing innovation and data privacy.
Take the first step today. Try Alleo for free and transform your software adoption process, enhancing your IT policy for software adoption.