Best Practices for IT Managers: A Comprehensive Guide to Evaluating Cloud Vendor DDoS Protection
What if a major event you planned faced unexpected downtime due to DDoS attacks? Effective cloud DDoS protection evaluation is essential for preventing such scenarios.
As a life coach, I’ve helped many professionals navigate these challenges. In my experience, effective risk assessment and cybersecurity risk management are crucial for IT infrastructure protection.
In this article, you’ll discover best practices for evaluating cloud vendor DDoS protection. We’ll cover DDoS mitigation strategies, benefits, and tools to help you with network traffic analysis and real-time threat monitoring. We’ll also explore service level agreements (SLAs) for DDoS and conduct a cloud vendor comparison.
Let’s dive into scalable DDoS defense and cost-effective cloud protection strategies.

Challenges of Assessing Cloud DDoS Protection
Understanding how to evaluate Cloud DDoS protection can be daunting. Many IT managers and event planners struggle with this cloud security assessment initially.
Inadequate DDoS protection can disrupt event planning and execution. Imagine the chaos if your major event faces unexpected downtime due to insufficient cybersecurity risk management.
Several clients report feeling overwhelmed by the technical details of Cloud DDoS protection evaluation. They find it hard to assess traffic filtering and attack detection mechanisms in network traffic analysis.
You need clear, actionable steps to navigate this complex process of IT infrastructure protection. From my experience, thorough evaluation and testing of DDoS mitigation strategies are essential for peace of mind.
The severity of DDoS attacks demands a proactive approach to scalable DDoS defense. Your event’s success depends on effective cloud vendor comparison and cost-effective cloud protection.

Roadmap to Evaluating Cloud Vendor DDoS Protection
Overcoming this challenge requires a few key steps. Here are the main areas to focus on for an effective Cloud DDoS protection evaluation:
- Evaluate Vendor’s DDoS Mitigation Strategies: Request documentation, conduct simulated attacks, and review third-party evaluations for IT infrastructure protection.
- Review Cloud Provider’s Security Certifications: Verify compliance, assess certification recency, and request audit evidence as part of your cloud security assessment.
- Assess Vendor’s Incident Response Procedures: Review plans, evaluate team qualifications, and conduct tabletop exercises for cybersecurity risk management.
- Analyze Traffic Filtering and Rate Limiting: Examine filtering mechanisms, assess rate limiting, and test during peak periods for network traffic analysis.
- Compare Cloud-Based Anti-DDoS Service Options: Research services, request trials, and analyze integration capabilities for scalable DDoS defense.
- Verify Vendor’s Compliance with Security Standards: Review compliance, request assessments, and ensure continuous monitoring, including Service Level Agreements (SLAs) for DDoS protection.
Let’s dive into this Cloud DDoS protection evaluation roadmap!
1: Evaluate vendor’s DDoS mitigation capabilities
Evaluating a vendor’s DDoS mitigation capabilities is essential for ensuring robust event protection and conducting a thorough cloud DDoS protection evaluation.
Actionable Steps:
- Request comprehensive documentation on the vendor’s DDoS mitigation strategies and cloud security assessment procedures.
- Conduct simulated DDoS attack scenarios to test the vendor’s IT infrastructure protection capabilities.
- Review third-party evaluations and case studies of the vendor’s past DDoS mitigation performance and network traffic analysis.
Explanation: These steps matter because they provide a clear understanding of the vendor’s ability to handle DDoS attacks and implement scalable DDoS defense measures.
Ensuring that the vendor has a proven track record and reliable mitigation strategies helps in making informed decisions about cybersecurity risk management.
For more detailed insights, you can refer to Palo Alto Networks’ resource on DDoS attacks.
Taking these measures will give you peace of mind during your event planning process and help in selecting cost-effective cloud protection solutions.

2: Review cloud provider’s security certifications
Reviewing cloud provider’s security certifications is critical to ensure they meet industry standards for protecting against DDoS attacks. This step is essential in your cloud DDoS protection evaluation process.
Actionable Steps:
- Verify compliance with industry-standard certifications. Check for ISO/IEC 27001, SOC 2, and NIST certifications as part of your cloud security assessment.
- Assess the recency and scope of certifications. Ensure they cover all aspects of DDoS mitigation strategies and IT infrastructure protection, and are up-to-date.
- Request evidence of ongoing compliance. Look for recent audit reports and continuous improvement processes in network traffic analysis and cybersecurity risk management.
Key aspects to consider when reviewing certifications:
- Relevance to DDoS protection
- Frequency of audits
- Scope of certification coverage
Explanation: These steps matter because they confirm the vendor’s adherence to recognized security standards. This ensures your event is safeguarded by reliable and certified practices, including scalable DDoS defense and real-time threat monitoring.
For more information, you can refer to FDIC’s guidance on risk management in cloud computing.
Taking these steps helps you confidently trust your vendor’s security measures and service level agreements (SLAs) for DDoS protection. It’s an essential part of your cloud vendor comparison for cost-effective cloud protection.

3: Assess vendor’s incident response procedures
Evaluating incident response procedures is vital for ensuring quick and effective mitigation of DDoS attacks as part of your cloud DDoS protection evaluation.
Actionable Steps:
- Review the vendor’s incident response plan. Ensure it includes steps for DDoS attack detection, response, and recovery, focusing on cloud security assessment and IT infrastructure protection.
- Evaluate the incident response team’s qualifications. Check for relevant certifications and experience in handling DDoS incidents and implementing DDoS mitigation strategies.
- Conduct a tabletop exercise. Simulate a DDoS attack to assess the effectiveness of the incident response plan and real-time threat monitoring capabilities.
Explanation: These steps matter because they confirm the vendor’s preparedness and ability to manage DDoS incidents efficiently, which is crucial for cybersecurity risk management.
Ensuring a qualified team and a robust plan can significantly mitigate risks. For more guidance, refer to the FDIC’s risk management resource.
Taking these steps ensures your event remains secure and uninterrupted, leveraging scalable DDoS defense and cost-effective cloud protection.

4: Analyze traffic filtering and rate limiting
Analyzing traffic filtering and rate limiting is crucial for ensuring effective DDoS protection for your events as part of a comprehensive cloud DDoS protection evaluation.
Actionable Steps:
- Examine the vendor’s traffic filtering mechanisms. Ensure they include both automated and manual filtering options to handle various attack vectors, which is essential for robust DDoS mitigation strategies.
- Assess the rate limiting capabilities of the vendor. Check for customizable rate limiting policies that can adapt to different traffic patterns and ensure optimal performance, a key aspect of IT infrastructure protection.
- Test the vendor’s ability to filter and limit traffic during peak usage periods. Schedule these tests during high-traffic events to evaluate real-world performance, which is crucial for network traffic analysis and scalable DDoS defense.
Explanation: These steps matter because they ensure your vendor can efficiently manage and mitigate DDoS attacks. Effective traffic filtering and rate limiting are essential for maintaining service availability during high-stress periods, contributing to comprehensive cybersecurity risk management.
For more insights, you can refer to Palo Alto Networks’ resource on DDoS attacks and mitigation techniques.
Implementing these measures will help you achieve better protection for your events and improve your overall cloud DDoS protection evaluation.

5: Compare cloud-based anti-DDoS service options
Evaluating different cloud-based anti-DDoS service options is vital for ensuring robust protection. A thorough cloud DDoS protection evaluation is essential for effective cybersecurity risk management.
Actionable Steps:
- Research and compare features. Look at pricing, customer reviews, and capabilities of services like AWS Shield, Cloudflare, and Akamai for comprehensive cloud security assessment.
- Request trial access. Test these services in your environment to assess their effectiveness in DDoS mitigation strategies.
- Analyze integration capabilities. Ensure seamless integration with your existing IT infrastructure protection without compromising performance.
Key factors to consider when comparing services:
- Scalability of protection for scalable DDoS defense
- Real-time threat intelligence and monitoring
- Customization options for network traffic analysis
Explanation: These steps matter because they help you identify the most suitable anti-DDoS service for your needs.
Comparing features and testing in real-world scenarios ensures you choose a reliable solution. For more information, check Palo Alto Networks’ resource on DDoS attacks.
Choosing the right service enhances your event’s security and minimizes downtime. Consider service level agreements (SLAs) for DDoS protection and conduct a thorough cloud vendor comparison for cost-effective cloud protection.

6: Verify vendor’s compliance with security standards
Ensuring your vendor complies with security standards is crucial for robust DDoS protection and a thorough cloud DDoS protection evaluation.
Actionable Steps:
- Conduct a thorough review of compliance documents. Examine the vendor’s adherence to standards such as NIST guidelines and other industry-specific requirements for IT infrastructure protection.
- Request third-party compliance assessments. Review independent audit reports to identify any gaps or areas of concern in cloud security assessment.
- Ensure continuous compliance monitoring. Verify the vendor has tools and procedures for ongoing compliance verification and improvement, including real-time threat monitoring.
Benefits of verifying compliance:
- Enhanced trust in vendor capabilities for DDoS mitigation strategies
- Reduced risk of security breaches through cybersecurity risk management
- Alignment with industry best practices for scalable DDoS defense
Explanation: These steps matter because they ensure your vendor meets recognized security standards, offering reliable protection for your events and cost-effective cloud protection.
Independent assessments provide an unbiased view of the vendor’s security posture and network traffic analysis capabilities. For detailed guidelines, refer to NIST’s publication on compliance standards.
Taking these steps helps you trust in your vendor’s security measures, ensuring peace of mind and effective cloud DDoS protection evaluation.
Next, we’ll explore how Alleo can assist in this evaluation process, including service level agreements (SLAs) for DDoS and cloud vendor comparison.

Partner with Alleo for Effective DDoS Protection
We’ve explored the challenges of cloud DDoS protection evaluation. Did you know you can work with Alleo to streamline this process and enhance your cybersecurity risk management?
Set up an account easily with Alleo. Create a personalized plan tailored to your IT infrastructure protection needs, including scalable DDoS defense strategies.
Our AI coach will guide you through every step of your cloud security assessment. It follows up on your progress and handles changes, ensuring comprehensive network traffic analysis.
Stay accountable with text and push notifications for real-time threat monitoring.
Ready to get started for free and improve your cost-effective cloud protection? Let me show you how!
Step 1: Access Your Account
Log in to your account or create a new one to begin evaluating cloud vendor DDoS protection with Alleo’s AI coach guidance.

Step 2: Choose “Building better habits and routines”
Select “Building better habits and routines” to develop a structured approach for assessing DDoS protection, ensuring you consistently evaluate vendors and maintain robust security practices for your events.

Step 3: Selecting the Career Life Area
Choose “Career” as your focus area to address DDoS protection challenges in event planning. This selection allows our AI coach to provide tailored guidance on evaluating cloud vendors, enhancing your professional skills in cybersecurity risk assessment, and ultimately safeguarding your events from potential disruptions.

Step 4: Starting a coaching session
Begin your journey with an intake session, where our AI coach will help you create a tailored plan for assessing cloud vendor DDoS protection, ensuring your events remain secure and uninterrupted.

Step 5: Viewing and managing goals after the session
After your coaching session, check the Alleo app’s home page to view and manage the DDoS protection goals you discussed, allowing you to track progress and make adjustments as needed.
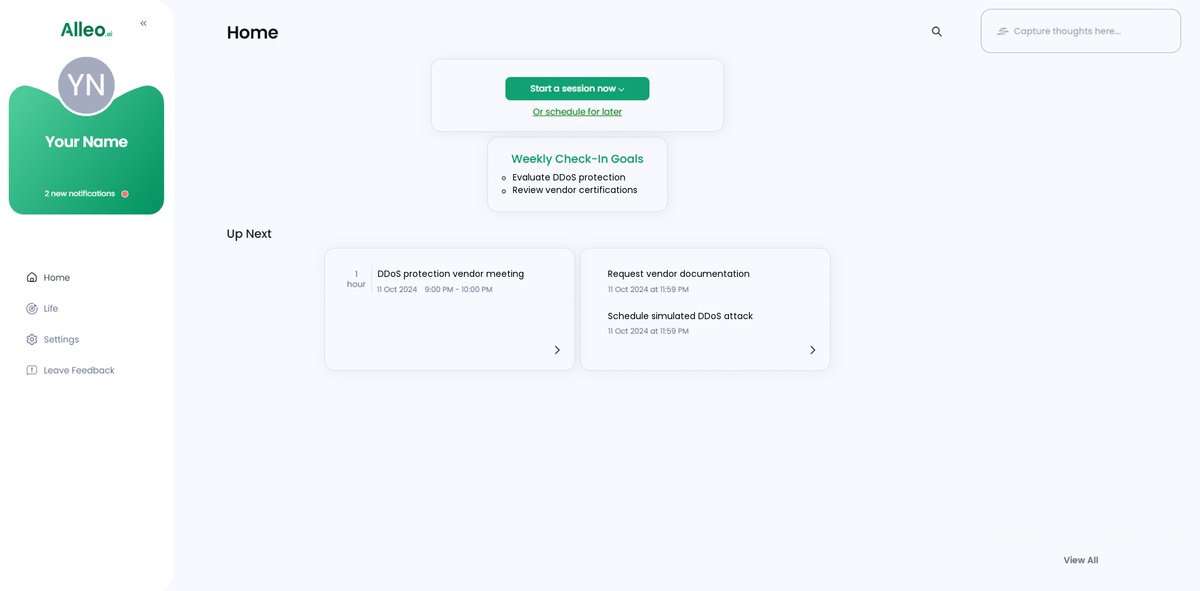
Step 6: Adding events to your calendar or app
Use Alleo’s calendar and task features to add your DDoS protection evaluation milestones, allowing you to easily track your progress in addressing this critical security concern for your event planning.
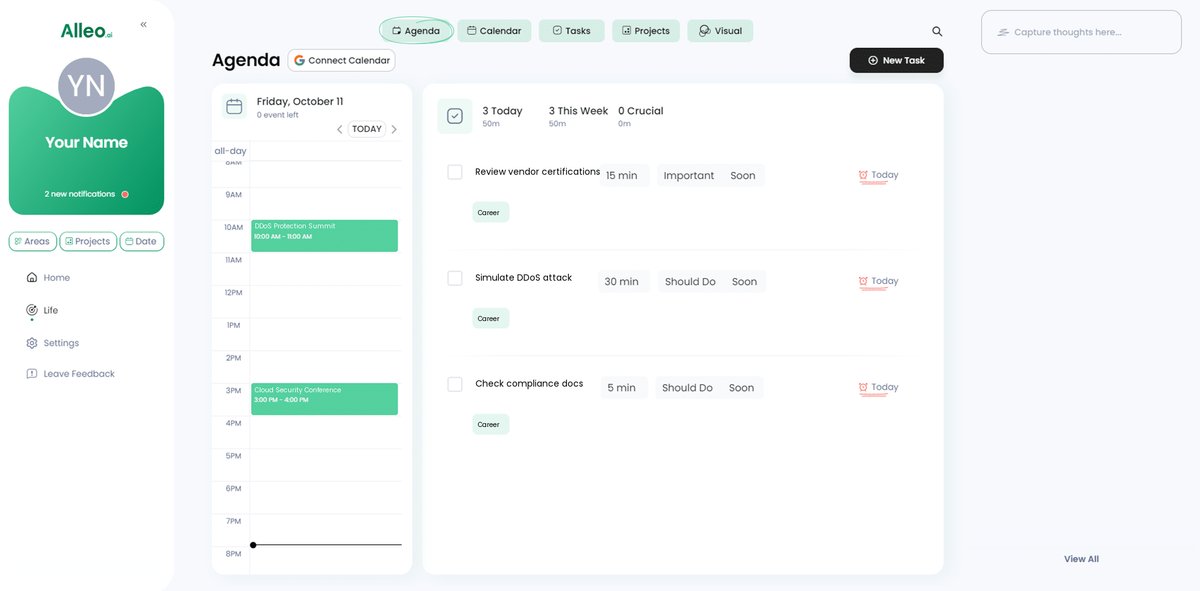
Final Thoughts on DDoS Protection for Event Planners
Assessing cloud DDoS protection evaluation is no small feat, but it’s crucial for your event’s success. By following the steps outlined, you can ensure robust IT infrastructure protection.
Remember, evaluating vendor capabilities, reviewing certifications, and understanding incident response plans are key to cloud security assessment. Analyzing network traffic analysis and rate limiting also plays a vital role in DDoS mitigation strategies.
Consider comparing cloud-based anti-DDoS services and verifying compliance with security standards. Each step brings you closer to effective cybersecurity risk management for a well-protected event.
I understand the challenges you face in this complex process of cloud DDoS protection evaluation. That’s why Alleo is here to help.
Alleo guides you through every step, making the evaluation process smoother and more effective. With personalized plans and AI coaching, you’re never alone in implementing scalable DDoS defense.
Take control of your event’s security today. Start with Alleo for free and experience peace of mind with cost-effective cloud protection and real-time threat monitoring.