How IT Managers Can Assess Cloud Vendor Security Risks in 4 Critical Steps
Have you ever faced the daunting task of conducting a cloud vendor security assessment, only to find your event data compromised?
As a life coach, I’ve guided many professionals through similar challenges in cloud security. It’s a critical but often overwhelming task, especially when considering multi-cloud security considerations.
In this article, you’ll learn actionable strategies to assess cloud vendor security risks. We’ll explore tools like HECVAT, continuous monitoring, third-party risk assessments for cloud services, and compliance checks. These elements form a crucial part of any cloud security assessment checklist.
Ready to secure your vendor relationships and improve data protection in cloud environments?
Let’s dive into cloud security best practices for IT managers.

Understanding the Challenges of Cloud Vendor Security Assessments
Evaluating cloud vendor security can be overwhelming for event planners. Many struggle to assess both the vendor and their cloud providers’ security measures, making cloud vendor security assessments a critical process.
Inadequate risk assessments can lead to severe consequences. These include data breaches, compliance issues, and significant reputational damage. Effective data protection in cloud environments is crucial.
Often, planners overlook continuous monitoring and third-party risk assessments for cloud services. This leaves their data vulnerable to emerging threats and compromises cloud security best practices for IT managers.
I’ve seen several clients initially miss critical security gaps. This often stems from insufficient evaluation and lack of ongoing risk management for cloud adoption.
By understanding these challenges, you can take actionable steps to secure your vendor relationships and improve your cloud service provider evaluation criteria.

A Roadmap to Secure Cloud Vendor Relationships
Overcoming this challenge requires a few key steps. Here are the main areas to focus on to make progress in your cloud vendor security assessment:
- Use HECVAT to Evaluate Cloud Vendor Security: Utilize the HECVAT questionnaire as part of your cloud security assessment checklist to comprehensively assess vendors’ security measures and data protection in cloud environments.
- Implement Continuous Vendor Risk Monitoring: Establish an ongoing framework to monitor and update risk assessments regularly, addressing multi-cloud security considerations and risk management for cloud adoption.
- Conduct Third-Party Security Assessments: Engage reputable auditors to perform thorough security evaluations, including third-party risk assessment for cloud services.
- Review Vendor’s Compliance Certifications: Verify and cross-check vendors’ compliance certifications to ensure adherence to industry standards and regulatory compliance in cloud computing.
Let’s dive in!
1: Use HECVAT to evaluate cloud vendor security
Using the HECVAT (Higher Education Community Vendor Assessment Toolkit) is critical for conducting a comprehensive cloud vendor security assessment.
Actionable Steps:
- Download the HECVAT questionnaire: Obtain the latest version from a trusted source like the Upguard website. Set a timeline for completion as part of your cloud security assessment checklist.
- Engage with vendors: Schedule meetings to discuss and complete the HECVAT questionnaire. Ensure all relevant security aspects, including data protection in cloud environments and vendor compliance and certifications, are covered.
- Analyze responses: Use a scoring matrix to quantify and prioritize risks. Develop a report summarizing findings and action plans, considering cloud service provider evaluation criteria.
Explanation:
These steps matter because they help identify and mitigate potential security gaps. By using HECVAT for cloud vendor security assessment, you ensure a thorough evaluation of vendors’ security practices, aligning with industry standards and regulatory compliance in cloud computing.
This proactive approach can significantly reduce risks associated with cloud vendors, enhancing your overall security posture and supporting risk management for cloud adoption.
Key benefits of using HECVAT include:
- Standardized assessment process
- Comprehensive security evaluation
- Improved risk management
Ready to dive deeper into securing your vendor relationships?
Let’s move to the next step!

2: Implement continuous vendor risk monitoring
Continuous vendor risk monitoring is vital to detect any emerging threats and maintain security in cloud vendor security assessments.
Actionable Steps:
- Integrate automated monitoring tools: Implement tools that track vendor security performance continuously. Set specific metrics to measure effectiveness in cloud service provider evaluation.
- Schedule periodic reviews: Regularly review and update risk assessments. Timely detection of emerging risks is crucial for cloud security best practices.
- Foster open communication: Hold regular check-in meetings with vendors to discuss changes in their security posture. Develop a shared dashboard for real-time monitoring of cloud vendor security assessments.
Explanation:
These steps ensure ongoing vigilance and adaptability, crucial for maintaining security. Continuous monitoring helps identify new threats and adapt to evolving risks in cloud environments.
For more insight, explore the importance of continuous monitoring in this guide.
By staying proactive, you can effectively mitigate risks and enhance your security posture in cloud computing.
Let’s move on to the next crucial step!

3: Conduct third-party security assessments
Conducting third-party cloud vendor security assessments is crucial to ensure your vendors maintain robust security measures.
Actionable Steps:
- Identify reputable third-party auditors: Research and shortlist auditors with proven expertise in cloud security assessments. Verify their certifications and past performance in evaluating cloud service provider evaluation criteria.
- Schedule and conduct assessments: Plan the assessment process with the selected auditors. Ensure they examine critical areas, including data protection in cloud environments and incident response plans.
- Review and act on findings: Create a detailed action plan based on the auditor’s recommendations. Implement necessary security improvements and track progress to enhance risk management for cloud adoption.
Explanation:
These steps matter because they help you gain an unbiased perspective on your vendor’s security posture. External auditors bring expertise and thoroughness that may uncover hidden vulnerabilities in multi-cloud security considerations.
For further insights on vendor risk management, explore this comprehensive guide. By conducting third-party cloud vendor security assessments, you can significantly enhance your vendor security strategy and maintain compliance with industry standards and regulatory compliance in cloud computing.
Key areas to focus on during third-party assessments:
- Data protection practices
- Incident response procedures
- Access control measures
Let’s move on to the next crucial step!

4: Review vendor’s compliance certifications
Reviewing vendor compliance certifications is essential to ensure their adherence to industry standards and regulations as part of your cloud vendor security assessment.
Actionable Steps:
- Request and review certifications: Obtain copies of certifications like ISO 27001, SOC 2, and PCI-DSS from vendors. Verify their validity and scope as part of your cloud security assessment checklist.
- Cross-check against industry standards: Compare vendor certifications with industry best practices and regulatory compliance in cloud computing. Identify any gaps or areas for further scrutiny in your cloud service provider evaluation criteria.
- Set up continuous monitoring: Establish a compliance calendar to track certification renewals and audits. Conduct periodic reviews to maintain security standards and ensure data protection in cloud environments.
Explanation:
These steps help ensure your vendors meet industry standards, reducing risks and enhancing security as part of your third-party risk assessment for cloud services.
For further insight, explore the importance of compliance in this guide.
By staying vigilant, you can maintain robust security and compliance, protecting your data from potential threats in multi-cloud security considerations.
By following these steps, you can strengthen your vendor relationships and safeguard your data effectively, adhering to cloud security best practices for IT managers.

Partner with Alleo to Secure Your Cloud Vendor Relationships
We’ve explored the challenges of cloud vendor security assessment and detailed actionable steps. Did you know you can work directly with Alleo to make this journey easier and faster?
Setting up an account with Alleo is simple. Create a personalized plan tailored to your needs, including a cloud security assessment checklist.
Alleo’s AI coach will guide you through each step, ensuring you stay on track with cloud vendor security assessment. Get automated reminders, risk management tools for cloud adoption, and real-time progress updates.
Alleo keeps you accountable with text and push notifications, helping you maintain cloud security best practices for IT managers.
Ready to get started for free? Let me show you how to begin your cloud vendor security assessment journey!
Step 1: Log In or Create Your Account
To start securing your cloud vendor relationships, log in to your Alleo account or create a new one to access the AI coach and risk assessment tools.

Step 2: Choose “Building better habits and routines”
Select “Building better habits and routines” to create a structured approach for assessing and improving your cloud vendor security practices, helping you develop consistent and effective risk management processes.

Step 3: Select “Career” as Your Focus Area
Choose “Career” as your focus area to address cloud vendor security challenges, as this directly impacts your professional responsibilities and helps safeguard your organization’s data and reputation.

Step 4: Starting a coaching session
Begin your journey with Alleo by scheduling an intake session to create a personalized plan for assessing and securing your cloud vendor relationships.

Step 5: Viewing and managing goals after the session
After your coaching session on cloud vendor security, check the Alleo app’s home page to view and manage the goals you discussed, helping you stay on track with implementing your security assessment strategies.
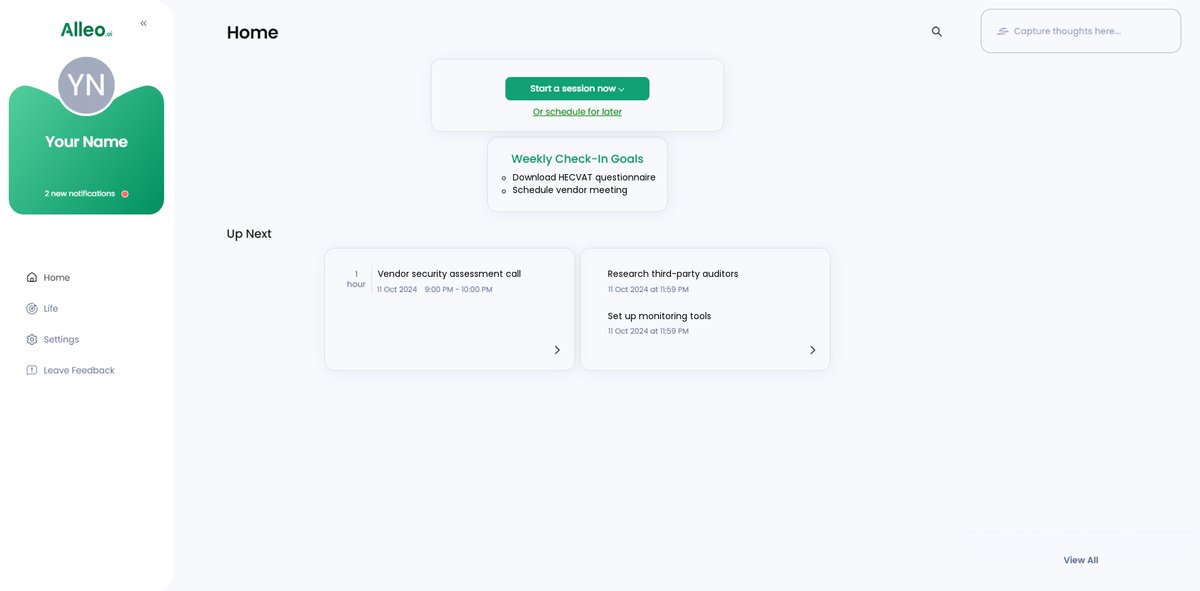
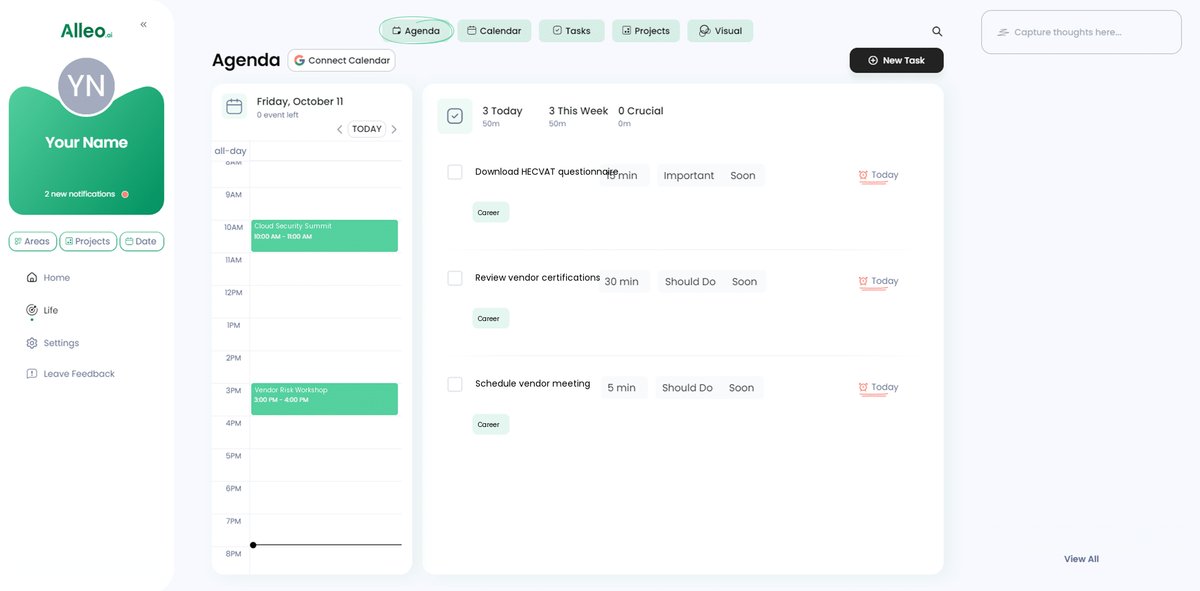
Step 6: Adding events to your calendar or app
Use Alleo’s calendar and task features to schedule and track your vendor security assessment activities, ensuring you stay on top of evaluations, monitoring, and compliance checks for each cloud vendor relationship.
Wrapping Up: Strengthen Your Cloud Vendor Security
As we’ve seen, conducting a thorough cloud vendor security assessment is essential for protecting your data in cloud environments.
By using tools like HECVAT, continuous monitoring, third-party risk assessments, and reviewing vendor compliance and certifications, you can mitigate potential threats and improve your cloud security assessment checklist.
It’s crucial to stay proactive and vigilant in these efforts to protect your organization from data breaches and regulatory compliance issues in cloud computing.
Empathizing with your challenges, I know it can be daunting, but taking these steps will make a significant difference in your cloud service provider evaluation criteria.
Remember, you don’t have to handle cloud vendor security assessments alone.
Alleo is here to help, guiding you with actionable advice on cloud security best practices for IT managers and ensuring you stay on track with multi-cloud security considerations.
Try Alleo for free today and secure your cloud vendor relationships with confidence, improving your risk management for cloud adoption.