Project Manager’s Ultimate Guide to Cybersecurity Across Multiple Platforms
Are you struggling to manage cybersecurity across diverse platforms in your complex project environment? Project cybersecurity best practices are essential for navigating these challenges effectively.
As a life coach, I’ve helped many project managers tackle these exact challenges. In my experience, cohesive cross-platform security strategies are essential for successful project management in cybersecurity.
In this article, you’ll discover best practices for handling cybersecurity in your projects. We’ll cover strategies like multi-factor authentication, multi-platform risk assessments, and more to enhance your cybersecurity project lifecycle.
Let’s dive in to explore these project cybersecurity best practices.

Understanding the Cybersecurity Challenge
Handling cybersecurity across different platforms is incredibly complex. Each platform has unique vulnerabilities and security requirements, making project cybersecurity best practices essential for effective cross-platform security strategies.
Coordinating these can be a nightmare, especially when implementing multi-platform risk assessment.
Many clients initially struggle to unify security measures within the cybersecurity project lifecycle. This disjointed approach leads to gaps that cybercriminals exploit.
The stakes are high in project management in cybersecurity.
Poor cybersecurity practices can result in data breaches, financial loss, and reputational damage. In my experience, the consequences are severe, highlighting the importance of robust incident response coordination.
You need robust cybersecurity measures that align with project cybersecurity best practices. Let’s explore practical solutions to tackle these challenges effectively, considering resource allocation for multi-platform security.

Key Steps to Strengthen Cybersecurity Across Multiple Platforms
Overcoming this challenge requires a few key steps. Here are the main areas to focus on to make progress in implementing project cybersecurity best practices.
- Implement multi-factor authentication across platforms: Start with critical systems and monitor regularly as part of your cross-platform security strategies.
- Conduct regular cross-platform risk assessments: Schedule quarterly sessions and use a standardized template to support project management in cybersecurity.
- Establish standardized incident response playbooks: Create playbooks for different incidents and conduct regular drills to enhance incident response coordination.
- Integrate cybersecurity into CI/CD pipelines: Include security checks and automate vulnerability scanning throughout the cybersecurity project lifecycle.
- Provide role-based cybersecurity training: Organize workshops and ensure ongoing support to improve stakeholder communication in cybersecurity projects.
Let’s dive in!
1: Implement multi-factor authentication across platforms
Multi-factor authentication (MFA) is crucial for securing your project’s diverse platforms and is a key component of project cybersecurity best practices.
Actionable Steps:
- Conduct an audit of all current authentication methods across platforms.
- Create a checklist of all platforms and their authentication methods.
- Set a two-week timeline for this audit, aligning with the cybersecurity project lifecycle.
- Roll out multi-factor authentication starting with the most critical systems.
- Prioritize systems based on their importance and vulnerability, utilizing multi-platform risk assessment.
- Implement MFA in phases, starting with a pilot group, following agile methodologies in security projects.
- Monitor and review MFA implementation regularly.
- Set up a monitoring system to track and report on MFA usage, incorporating performance metrics for cybersecurity projects.
- Schedule monthly review meetings to discuss findings and ensure stakeholder communication in cybersecurity.
Key benefits of implementing MFA as part of project cybersecurity best practices include:
- Enhanced security against unauthorized access
- Reduced risk of data breaches
- Improved compliance with industry standards and security compliance across platforms
Explanation: Implementing MFA significantly reduces the risk of unauthorized access, ensuring that even if one factor is compromised, another layer of security remains, which is essential for cross-platform security strategies.
According to FEMA, multi-factor authentication is an essential element in protecting critical systems.
Regular monitoring and phased rollout help maintain security across all platforms, supporting effective project management in cybersecurity.
Let’s move on to the next crucial step in project cybersecurity best practices.

2: Conduct regular cross-platform risk assessments
Regular risk assessments are vital for identifying vulnerabilities across different platforms, a key aspect of project cybersecurity best practices.
Actionable Steps:
- Schedule quarterly risk assessment sessions.
- Create a calendar with set dates for assessments, aligning with the cybersecurity project lifecycle.
- Allocate sufficient time and resources for each session, considering resource allocation for multi-platform security.
- Develop a standardized risk assessment template.
- Collaborate with cybersecurity experts to create the template, incorporating cross-platform security strategies.
- Ensure the template is user-friendly and adaptable for multi-platform risk assessment.
- Assign dedicated risk assessment roles within the team.
- Identify team members with the right expertise in project management in cybersecurity and train them.
- Provide ongoing support and resources for these roles, focusing on security compliance across platforms.
Explanation: Regular risk assessments help in proactively identifying and mitigating potential threats. This process ensures that all platforms are secure and compliant with industry standards, supporting project cybersecurity best practices.
According to AuditBoard, integrating risk management across various compliance frameworks is essential for effective cybersecurity. Regular assessments and dedicated roles ensure thorough and consistent evaluations, which is crucial for stakeholder communication in cybersecurity projects.
This foundational step sets the stage for establishing standardized incident response playbooks and enhancing incident response coordination.

3: Establish standardized incident response playbooks
Creating standardized incident response playbooks is crucial for efficient and effective handling of cybersecurity incidents, aligning with project cybersecurity best practices.
Actionable Steps:
- Develop playbooks for various incident types.
- Identify common incident scenarios and draft specific response procedures, considering cross-platform security strategies.
- Start with high-priority incidents and gradually cover all scenarios, incorporating multi-platform risk assessment.
- Conduct regular incident response drills.
- Schedule bi-annual drills to test the effectiveness of the playbooks, aligning with the cybersecurity project lifecycle.
- Use feedback from these drills to refine and improve the procedures, employing agile methodologies in security projects.
- Review and update playbooks annually.
- Set up an annual review process involving key stakeholders, focusing on stakeholder communication in cybersecurity.
- Ensure updates reflect the latest threats and best practices in project cybersecurity.
Essential components of an effective incident response playbook:
- Clear roles and responsibilities
- Step-by-step response procedures
- Communication protocols for incident response coordination
- Post-incident analysis guidelines, including performance metrics for cybersecurity projects
Explanation: Standardized incident response playbooks ensure a coordinated and effective response to cybersecurity incidents. Regular drills and updates help teams stay prepared and responsive, adhering to project cybersecurity best practices.
According to Executive Order 14028, standardized incident response is key to improving cybersecurity across federal agencies.
This step paves the way for integrating cybersecurity into CI/CD pipelines, enhancing security compliance across platforms.

4: Integrate cybersecurity into CI/CD pipelines
Integrating cybersecurity into CI/CD pipelines is essential for securing the software development lifecycle and implementing project cybersecurity best practices.
Actionable Steps:
- Embed security checks at each stage of the CI/CD pipeline.
- Collaborate with DevOps to ensure security is integrated, aligning with project management in cybersecurity.
- Start with critical stages and expand gradually, considering cross-platform security strategies.
- Automate vulnerability scanning in the CI/CD process.
- Deploy tools for regular automated scans, supporting multi-platform risk assessment.
- Ensure tools are correctly configured and maintained throughout the cybersecurity project lifecycle.
- Train developers on secure coding practices.
- Organize workshops and provide resources, incorporating agile methodologies in security projects.
- Include secure coding in onboarding for new developers, emphasizing stakeholder communication in cybersecurity.
Explanation: These steps ensure continuous security throughout the development process. By embedding security checks, automating vulnerability scans, and training developers, you significantly reduce risks and enhance project cybersecurity best practices.
According to NICE Framework, integrating security into CI/CD pipelines is crucial for maintaining robust cybersecurity.
This approach ensures a secure development environment, paving the way for effective project management in cybersecurity and resource allocation for multi-platform security.

5: Provide role-based cybersecurity training
Providing role-based cybersecurity training is crucial for ensuring that every team member understands their specific security responsibilities in project cybersecurity best practices.
Actionable Steps:
- Develop customized training modules for different roles within your team.
- Collaborate with cybersecurity experts to create tailored content for project management in cybersecurity.
- Ensure that the training is relevant and easy to understand across multi-platform environments.
- Schedule regular training sessions and refreshers.
- Set up a calendar with quarterly training dates aligned with the cybersecurity project lifecycle.
- Include interactive elements like simulations and quizzes on cross-platform security strategies.
- Monitor and assess the effectiveness of the training.
- Collect feedback from participants to improve future sessions on multi-platform risk assessment.
- Track implementation of learned practices through regular audits of project cybersecurity best practices.
Key outcomes of effective role-based cybersecurity training:
- Improved security awareness across the organization
- Faster identification and response to potential threats in the cybersecurity project lifecycle
- Reduced human error in security practices and stakeholder communication in cybersecurity
Explanation: Tailored training ensures that each team member is equipped with the knowledge they need to protect your project using project cybersecurity best practices.
According to NICE Framework, role-based training is essential for maintaining robust cybersecurity.
Regular sessions and feedback loops help keep the team updated on the latest threats and practices, including agile methodologies in security projects.
By focusing on role-based training, you will create a well-informed team that can effectively manage cybersecurity risks and implement project cybersecurity best practices.

Work with Alleo to Secure Your Projects
We’ve explored the challenges of managing cybersecurity across multiple platforms. But did you know you can work directly with Alleo to simplify this journey and implement project cybersecurity best practices?
With Alleo, you get tailored coaching support to handle cybersecurity risks and enhance project management in cybersecurity. Setting up an account is easy and quick.
Create a personalized plan to address specific challenges, including cross-platform security strategies and multi-platform risk assessment.
Our AI coach provides full sessions like any human coach, ensuring you stay on track with the cybersecurity project lifecycle. Follow-ups, progress checks, and accountability are managed via text and push notifications, supporting agile methodologies in security projects.
Ready to get started for free and improve your stakeholder communication in cybersecurity?
Let me show you how!
Step 1: Log In or Create Your Account
To begin securing your projects across multiple platforms, log in to your Alleo account or create a new one to access personalized cybersecurity coaching and support.

Step 2: Choose Your Cybersecurity Goal
Select “Setting and achieving personal or professional goals” to focus on strengthening your project’s cybersecurity measures across multiple platforms. By choosing this goal, you’ll receive tailored guidance on implementing the key strategies discussed, such as multi-factor authentication and risk assessments, to effectively protect your projects from cyber threats.

Step 3: Select “Career” as Your Focus Area
Choose “Career” as your focus area to tackle cybersecurity challenges in your project management role, aligning your professional growth with the critical security skills needed to protect your projects across multiple platforms.

Step 4: Starting a Coaching Session
Begin your cybersecurity journey with an intake session, where you’ll discuss your project’s unique challenges and set up a personalized plan to strengthen your cross-platform security measures.

Step 5: Viewing and managing goals after the session
After your cybersecurity coaching session, check the Alleo app’s home page to review and manage the goals you discussed, helping you stay on track with implementing crucial security measures across your project platforms.
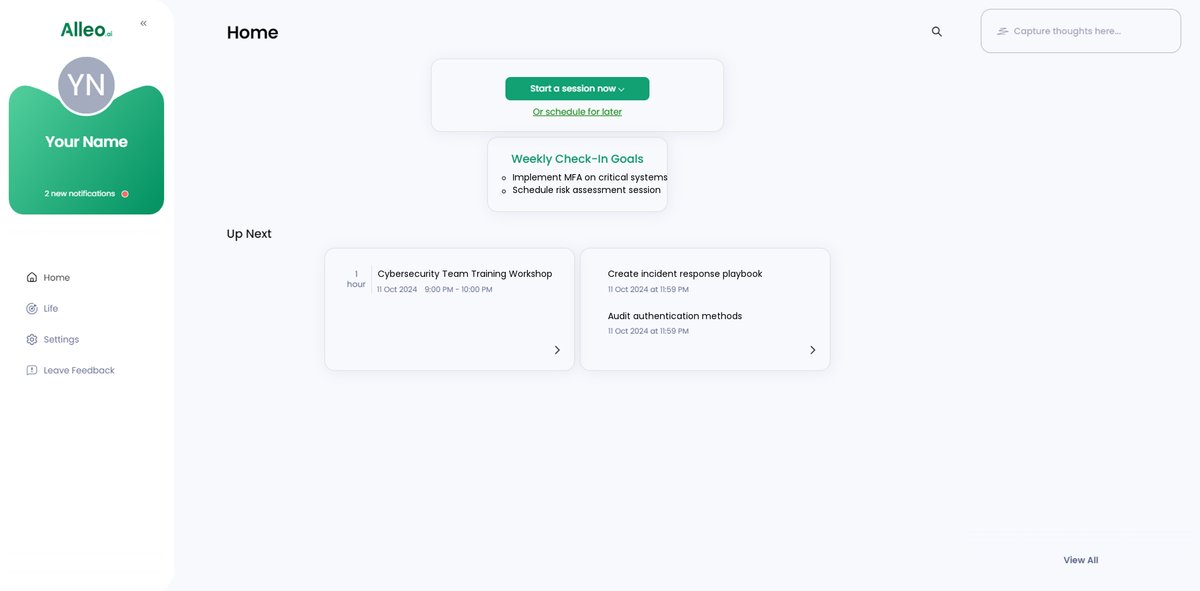
Step 6: Adding events to your calendar or app
To track your progress in implementing cybersecurity measures across platforms, use the Alleo app’s calendar and task features to schedule and monitor important events like MFA rollouts, risk assessments, and training sessions.
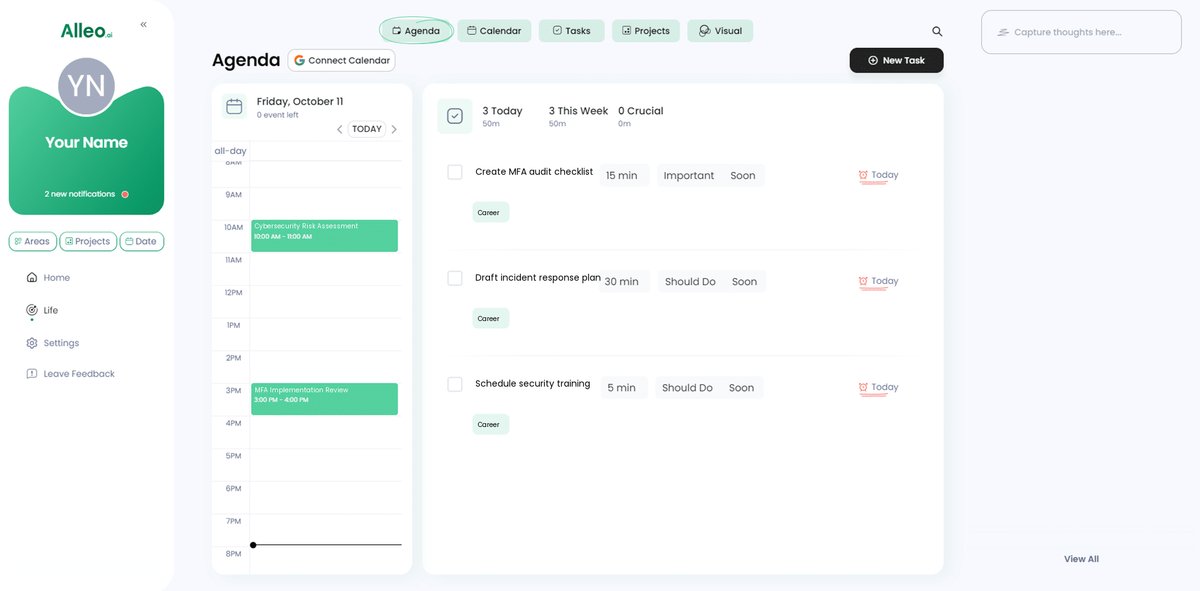
Wrapping Up Your Cybersecurity Journey
Let’s bring everything together on project cybersecurity best practices.
Managing cybersecurity across multiple platforms is challenging, but you can succeed. We’ve covered essential steps like implementing MFA, conducting multi-platform risk assessments, and providing role-based training for stakeholder communication in cybersecurity.
Remember, each action you take strengthens your project’s security compliance across platforms.
Feeling overwhelmed is natural, but take it one step at a time. You don’t have to do this alone in project management in cybersecurity.
Alleo can guide you through these steps with tailored coaching and support for your cybersecurity project lifecycle.
Ready to tackle project cybersecurity best practices with confidence? Start your journey with Alleo today.
It’s time to secure your projects and protect your investments with cross-platform security strategies. Try Alleo for free and experience the difference in your security compliance across platforms.